This article was originally published on the Metered Blog: NAT traversal: How does it work?
What is NAT (Network Address Translation) and its importance in modern networking.
The challenge of NAT traversal and why it is important for apps that require p2p connections.
Section 1: Understanding NAT and Its Implications
Types of NAT: Explain Static, Dynamic, and PAT (Port Address Translation), including diagrams for clarity.
How NAT Works: A step-by-step walkthrough of the NAT process, using real-life scenarios.
Challenges Introduced by NAT: Addressing issues like IP masquerading, port mapping complexities, and the impact on peer-to-peer (P2P) applications.
Section 2: The Main Solution - NAT Traversal Techniques
Basic Concepts: Introduction to NAT traversal, explaining terminologies such as public and private IP addresses, port forwarding, and UPnP (Universal Plug and Play).
Techniques Explored:
STUN (Session Traversal Utilities for NAT): Explaining the protocol with practical coding examples in Python and JavaScript.
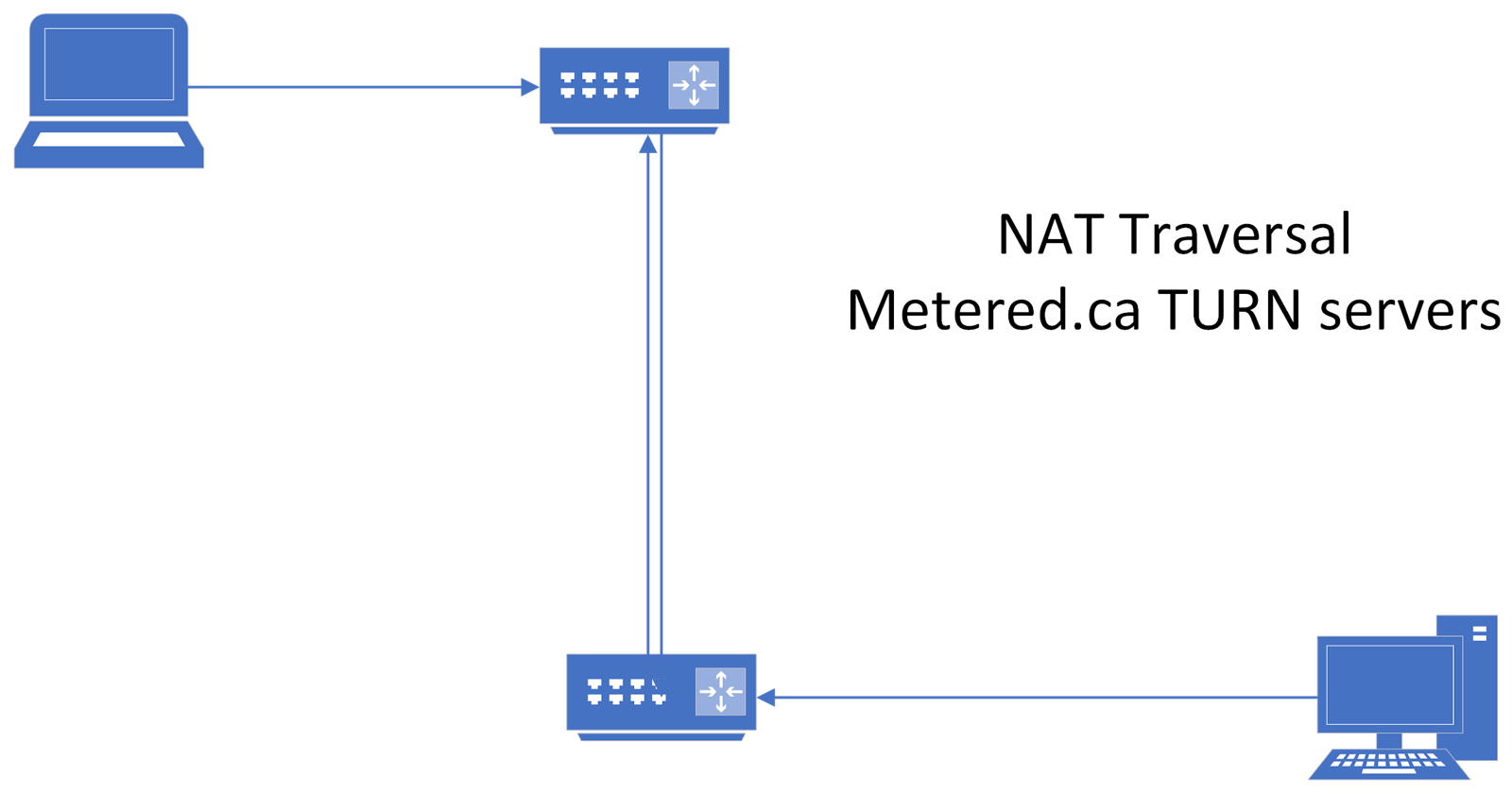
TURN (Traversal Using Relays around NAT): When STUN isn't enough, incorporating TURN with examples in Node.js.
ICE (Interactive Connectivity Establishment): Combining STUN and TURN for robust connectivity, demonstrated through WebRTC examples.
Different types of NAT and their explanation
Section 3: Implementing NAT Traversal in Modern Applications
Real-world Application Scenarios: Discussing scenarios like VoIP, online gaming, and P2P file sharing where NAT traversal is crucial.
Using TURN server providers such as Metered.ca TURN service
Network Address Translation (NAT): Overview and Importance
NAT is an important technology using which multiple devices (that are on a local network) can connect to the internet using a single Public IP address.
This came to be because there are a limited number of IPv4 Addreesses (this was before the advent of IPv6) and without NAT we would have run out of IPv$ addresses a long time ago
NAT works by translating the local IP address of the devices that are behind the NAT to a single public IP address and vice versa
Whenever a device which is on the local network wants to connect (send and revieve data) to the internet, the NAT device usually a router sends the data through its own public IP address.
The router does this by replacing the local IP address on the packet header with its own public IP address
The NAT device i.e the router then keeps track of this translation in a table, so that when the data comes back from the internet, it knows to which device it needs to send the data
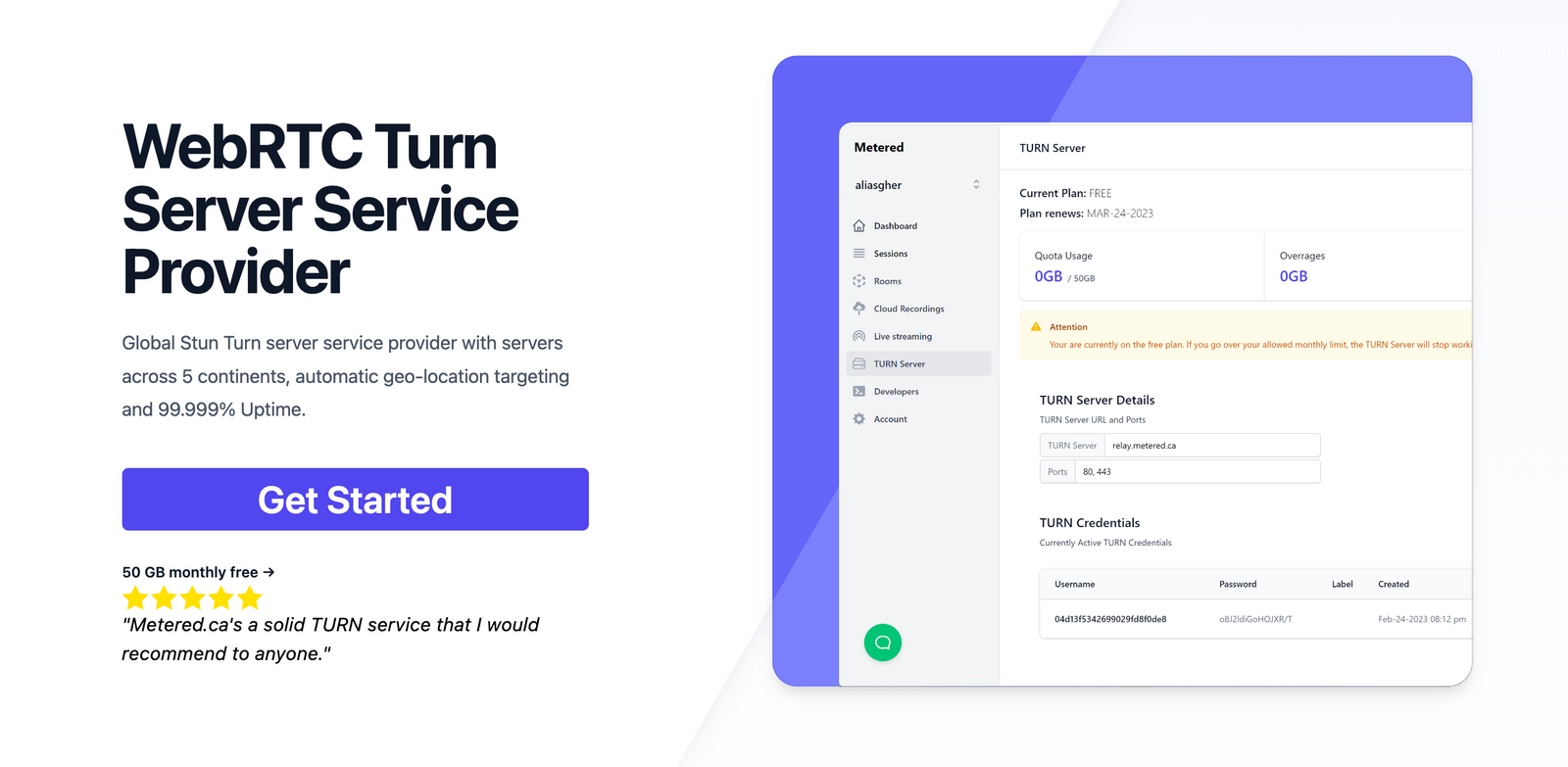
Metered TURN servers
Global Geo-Location targeting: Automatically directs traffic to the nearest servers, for lowest possible latency and highest quality performance. less than 50 ms latency anywhere around the world
Servers in 12 Regions of the world: Toronto, Miami, San Francisco, Amsterdam, London, Frankfurt, Bangalore, Singapore,Sydney, Seoul
Low Latency: less than 50 ms latency, anywhere across the world.
Cost-Effective: pay-as-you-go pricing with bandwidth and volume discounts available.
Easy Administration: Get usage logs, emails when accounts reach threshold limits, billing records and email and phone support.
Standards Compliant: Conforms to RFCs 5389, 5769, 5780, 5766, 6062, 6156, 5245, 5768, 6336, 6544, 5928 over UDP, TCP, TLS, and DTLS.
Multi‑Tenancy: Create multiple credentials and separate the usage by customer, or different apps. Get Usage logs, billing records and threshold alerts.
Enterprise Reliability: 99.999% Uptime with SLA.
Enterprise Scale: With no limit on concurrent traffic or total traffic. Metered TURN Servers provide Enterprise Scalability
50 GB/mo Free: Get 50 GB every month free TURN server usage with the Free Plan
Runs on port 80 and 443
Support TURNS + SSL to allow connections through deep packet inspection firewalls.
Support STUN
Supports both TCP and UDP
The challenge of NAT traversal and why it is important for apps that require p2p connections.
- Address Translation:
NAT modifies the IP address and the port number of the ongoing traffic and assigns a different public IP and port number.
For incoming traffic the NAT does the reverse translation based on the mapping table.
This process complecates the process of direct communication between devices that are between different NATs as they do not know the internal IP address and port number of each other
- Multiple NAT layers:
In many common scenarios there are multiple NATs involved.
There is usually a internet provider's NAT called the carrier NAT and there are also NAT routers at home and office as well
- Type of NAT
Section 1: Understanding NAT and Its Implications
Types of NAT: Explain Static, Dynamic, and PAT (Port Address Translation), including diagrams for clarity.
Static NAT: The static NAT is a type of NAT that translates the static private IP addresses to the public IP addresse on a one to one bases. This is used for devices which needs to be accessed directly from the internet such as web servers. The main advantage of the statuc NAT is that the public IP address remains contant.
Dynamic NAT: Unlike the static NAT the dynamic NAT assigns a public IP to the a private IP from a pool of local IP addresses on a first come and first serve basis. When a device disconnects from the internet that device's public IP and port number then becomes available to be assigned to another devie in the pool
PAT (Port Address Translation): PAT allows multiple devices on the local network to be mapped to a single IP address but with a unique port number. This is the most common type of NAT. It allows thousands of connections to be multiplexed over a single IP address that is available. PAT is specially important for small home or office networks where there is generally a single IP address assigned by ISP to these locations.
How NAT works
Initiating a Request: A device that is behind a NAT and in a private networks, wants to access a resource such as a website on the internet. The device initiates a request using a private IP address and a source port number.
NAT Translation: The NAT router recieves the request and translates the private IP address and port number to router's public IP and assigns a port number.
Forwarding the request: The NAT router then forwards the request to its destination on the internet. To the reciever of the request it appears that the request has originated from the router or the NAT device itself
Receiving a response: The web server that has received the request then responds back to the public IP address and port number that the request came from.
Back to the Private Network: The NAT router when it recieves the data from the remote server i.e from the internet it looks into the NAT table to translate the public IP and port number to the private IP and port number of the device which initiated the request in the first place and then sends
Challenges Introduced by NAT
The NAT plays an important role in IP address conservation but it also introduces challenges in communication as well especially in peer 2 peer communication
IP Masquerading: With NAT the IP address of the actual client is hidden, because the actual client is on a private network. This makes it diffucult to establish peer to peer connection or to initiate a connection by the external host
Port Mapping Complexities: With PAT the most commonly used NAT architecture, multiple devices share a single IP addresses and the devices are differentiated by port numbers.
Impact on P2P Applications: NAT disrupts p2p apps communication by not disclosing the real IP addreess and Port number to the communicating devices. It also obstructs communication between devices. To communicate between devices that are behind diffrent NATs we need the NAT traversal using STUN and TURN servers
Section 2: NAT Traversal
Basic concepts
Public and Private IP address: Public IP addresses are unique address across the internet that allows devices that are on the internet to find each other
Port Forwarding: This is a manual and rudimentary NAT traversal technique that works in a few special cases. Here specific port numbers are pre configured in the NAT router to forward incoming traffic to specific ports to inside devices inside the private network.
Techniques for NAT Traversal
- STUN:
STUN also called as Session Traversal Utilities for NAT is a protocol that helps devices that are behind a NAT to descover what their public IP and port number is (As the only router knows the public IP and assigns a public facing port number to each device.
A STUN server is used to get the public facing IP address and port number of the device. The device basically sends a request to the STUN server and the STUN server responds with the IP address and port number from which the request from the device came from in a format that the NAT router does not remove. Thus the device behind the NAT knows what its IP address and port number is
How STUN works
For a detailed knowledge of how the STUN server works refer to Stun Server: What is Session Traversal Utilities for NAT?
- TURN
The TURN is protocol that works when STUN server fails. Due to a variety of reasons including firewalls and Complicated NAT such as Symmetric NAT the connection between devices that are behind different NATs is not possible.
TURN servers relay the traffic between devices. In most of the cases TURN servers are required to relay traffic when you using WebRTC for video calling
If you are looking for TURN server then we recommend going with Metered TURN servers
ICE: ICE also called as Interactive Connectivity framework combines STUN and TURN to ensure the best possible connectivity between peers. The ICE framework first tries STUN and if it fails it falls back to TURN
How ICE works: During the initial phase of connection, both the clients gather connectivitiy options called as candidates, this includes direct connections, STUN and TURN options. Then both the clients share these options with each other starting with the most direct connection. that is they first try to establish a direct connection, if it fails they try to connect through STUN and if that fails then they try to connect through TURN
Different types of NAT and their explanation
Full Cone NAT:
Full cone NAT is the unrestricted NAT, once the internal IP address and port number is mapped to the external IP and PORT number , external devices can send the data to the internal device by sending the data on the external IP and Port number
It is the simplest type of NAT based on understanding and predictability
Implications connectivity:
NAT Traversal: Users and devices can easily connect and establish p2p connectivity and the traffic coming on the external IP address and PORT number is directly send to a perticular device
Security considerations: The full cone NAT can be a security risk because it allows for unsolicited external connections from any external device.
Restricted cone nat
This is similar to a full cone nat in the sense that the internal IP address are mapped to an external IP address. But in the Restricted cone the the incoming packets are only accepted from an external device if the internal device has first sent a request to it
Implications for connectivity
- Selective Connectivity:
Only the external hosts that have initially recieved a request for connectivity can connect with the internal devices in restricted cone NAT
- Moderate NAT traversal difficulty:
NAT traveral is a bit more difficult in the restricted cone NAT as compared to the full cone NAT because the internal devices must first request the connection to connect to an external device. The external device on itself cannot connect to the internal device
- Somewhat secure:
This provides a level of security against unsolicitated access because the internal device must first request the external device to connect with the external device. Which means the external device cannot connect with the internal device without solicitation.
Port restricted cone NAT
Similar to Restricted cone NAT, but it has a added security requirement that incoming packets must be come from the external source from the external IP and port number from which the internal device send the request from
This type of NAT increases even more security by restricting connections to only the external IP and PORT number from which the request from the internal device was sent through the NAT router.
Implications for connectivity:
Difficulty in NAT traversal: It becomes difficult to create p2p connections between two clients and do NAT traversal because the 1. client must forst make a request to connect. 2. external connection must be come from the external IP and port number from which the request was made.
Enhanced security: the requirement that the external packets must come from the same external IP address and port number creates enhanced security.
Symmetric NAT
Symmetric NAT is the most strict type of NAT there is. Each request from the same internal device results in a different external IP and port number mapping from the NAT device. This means that the internal IP and port number might remain constant but the external IP and port number changes with every request and connection that is established.
Implications for connectivity:
Highly difficult NAT traversal: It is very difficult to establish p2p connection with clients that are behind a symmetric NAT, for NAT traversal you need advanced TURN servers where the data is relayed using the NAT server.
High Security: The dynamica mapping policy that changes the external IP and port number with every connection limts the ability of the external hosts to communicate with the devices that are behind the NAT router. Thus providing a higher level of sercurity
Using TURN server service providers such as Metered TURN servers
Metered Global TURN servers are premier TURN server service with servers in 5 continents of the worlds and in 10 regions across the world
Metered has 99.999% Uptime SLA and a free plan with 50 GB monthly TURN server usage.
In this section we are going to leatn how to use Metered TURN servers for NAT traversal in your application.
Step 1: Go tometered.ca/stun-turnand create an account
go to the metered website and create a account by filling in the sign up form. After you have signed up, it asks you to create an app.
You can name the app anything you want then you land up on the TURN server section
Step 2: Use credentials or Use API
Here you can create the credentials manually or you can use the api to create the credentials
After you have ceated the credentials, you can copy the ice servers array from the instructions
You can also create multiple credentials for multiple users or apps and you can also name the credentials accordingly to your use-case
You can also select the region where you want the TURN server, or you can also choose the Global region where TURN server that are nearest to the user are used
you can also create credentials with the API and expire the credential when the meeting or the session is over.
Step 3: Test out the credentials
You can test out the credentials by clicking on the turn server test button on the dashboard
you can create a video call by pasting your credentials on the video app and do a video call on different browsers or on different computers to test out the functionality
here is the link to the turn test: https://turndemo.metered.ca/